This page includes:
About Microsoft 365 - ATO detection
If you have integrated Perception Point X‑Ray with Microsoft 365 [Inline or API], you can enhance your protection by enabling the Perception Point X‑Ray-Microsoft 365 ATO [account takeover] detection functionality. This functionality monitors user activity in your Microsoft 365 accounts to detect possible ATO attempts - based significantly on detecting anomalies in user behavior. It is recommended that you activate the Microsoft 365 ATO detection functionality in your organization.
|
Note: The ATO detection functionality is not available for Google Workspace, Exchange, and "Other" integrations. |
To activate the Microsoft 365 ATO detection functionality, mailbox auditing must be enabled in your Microsoft 365 account. Perception Point X‑Ray analyzes the Microsoft 365 audit log, and uses various algorithms to detect suspicious user activity. Suspicious user activity includes behavior such as:
-
creating suspicious mailbox rules [for example, forwarding, redirecting, moving, or deleting emails]
-
performing suspicious login attempts, such as too-fast-to-travel logins. In addition, Perception Point X‑Ray tries to identify unusual login patterns and login attempts from unfamiliar locations or devices.
Suspicious ATO activity appears as entries in the Cases page. For details about cases, see Cases.
|
IMPORTANT: After you activate ATO detection, we recommend that you also enable alerts for suspected ATO attempts. For details, see Alerts. |
-
You can activate Microsoft 365 ATO only if the Perception Point X‑Ray-Microsoft 365 integration [Inline or API] is already enabled in your organization. For details, see Connecting Microsoft 365.
|
Auto alerts |
If Perception Point X‑Ray detects a possible account takeover in your organization, Perception Point X‑Ray will send an email alert with a subject similar to "URGENT - Possible Account Take Over". The email will include details of the suspected account takeover. The email will be sent to the recipients that are specified in the "Alert via email on malicious cases" setting. If this setting is not enabled, email alerts will not be sent. [See Configuring alerts] Work together with the Perception Point IR Team to investigate and resolve the issue. |
|
Manual alerts |
The Perception Point IR Team monitors and reviews the cases that are added by Perception Point X‑Ray. The Perception Point IR Team may investigate any of the cases in more detail [typically High severity cases] and send an additional email alert with more details about the case.
|
More about ATO alerts
|
Licensing: |
There are no additional licensing requirements for enabling the ATO functionality. |
|
Note: |
ATO can't be enabled in bulk for multiple organizations - to activate ATO, it is necessary to perform the procedure below individually for each organization. |
|
Disclaimer: |
After you perform the procedures below to activate the ATO detection functionality, Perception Point X‑Ray will attempt to detect ATO attempts in all the email accounts in your organization. It is not possible to limit the ATO detection functionality to protect only specified domains, groups of users, or users. Please consider the associated privacy issues before implementing the ATO functionality. |
Configuring Microsoft 365 - ATO detection
|
|
Perform the following steps to configure the Microsoft 365 - ATO detection functionality.
This step enables mailbox auditing in Microsoft 365. If you have a Microsoft 365 E5 subscription, mailbox auditing may already be enabled for your organization. For more information about auditing, see the official Microsoft documentation  .
.
-
Open the Microsoft 365 Compliance Center at https://security.microsoft.com/auditlogsearch [Solutions > Audit].
-
Click "Start recording user and admin activity" near the top of the page.
Note:
-
Clicking the "Start recording user and admin activity" button enables mailbox auditing in Microsoft 365.
-
If this button doesn't appear, then mailbox auditing is probably already enabled for your organization - and you can continue with Step 2 below.
-
This step activates the ATO detection functionality in Perception Point X‑Ray. It must be performed by an admin user with the Admin role.
|
Note: Make sure to perform Step 2 in the [child] organization in which scans are performed - not in the parent organization. |
-
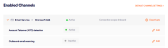
In Perception Point X‑Ray, in the left navigation menu, select Account > Bundles and Channels.
-
Under Enabled Channels, locate Email Service > Microsoft 365.
-
Under Email Service > Microsoft 365, locate Account Takeover (ATO) detection.
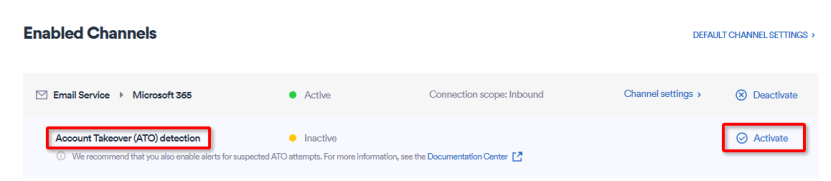
Note: If you don't see Account Takeover (ATO) detection, contact Perception Point Support.
-
Click Activate - on the right of Account Takeover (ATO) detection.
You'll be redirected to sign-in to your Microsoft account.
-
Sign-in to your Microsoft account as a global admin.
You'll see a list of the permissions that are required. -
Click Accept.
Microsoft 365 > Account Takeover (ATO) detection should now appear as Active in Perception Point X‑Ray.
IMPORTANT: After you activate ATO detection, we recommend that you also enable alerts for suspected ATO attempts - using the "Alert via email on malicious cases" setting. For details, see Configuring alerts.
From now on, Perception Point X‑Ray will try to detect ATO attempts in the Microsoft 365 email accounts in your organization. It is not necessary to inform Perception Point Support that ATO is activated.
Important: After you have completed this step, it may take up to 24 hours before audit data begins to be received by Perception Point X‑Ray. To ensure that the ATO detection functionality is correctly configured, after 24 hours, check that there are some ATO-detection related events in the Events page.
You should be able to see ATO-detection related events in the Events page in Perception Point X‑Ray. Look for events such as UserLoggedIn, New-InboxRule, and Set-InboxRule. For further details, see Events.
If you don't see any ATO-related events after 24 hours, contact Perception Point Support [support@perception-point.io] for assistance.
Monitoring ATO detections
You can use both the Cases page and the Events page to monitor suspected ATO attempts - the Cases page is the recommended location.
Monitoring in the Cases page
In the Cases page, you can monitor suspected ATO attempts in your organization.
For details about the Cases page, see Cases.
Monitoring in the Events page
In the Events page, you can monitor suspected ATO attempts in your organization. Each suspected ATO attempt is assigned a High severity in the Events page. The type of the event is:
-
For mailbox rule issues:
-
New-InboxRule
-
Remove-InboxRule
-
Set-InboxRule
-
Set-Mailbox
-
-
For login issues:
-
UserLoggedIn
-
UserLoginFailed
-
For details about the Events page, see Events.
A bit more about enabling ATO detection
-
ATO detection is performed in "near real-time" [not real-time]. The slight delay in detection occurs because Perception Point X‑Ray must wait for Microsoft to record the user actions in the audit log. It typically then takes a few minutes for Perception Point X‑Ray to receive audit log events, and only thereafter can the Perception Point X‑Ray ATO algorithms be performed on the audit log.
-
When ATO detection is first enabled, Perception Point X‑Ray will analyze the events that are available in Microsoft audit log. This may include events from the previous few days. Therefore ATO attempts may be detected even if the attempts were performed a few days prior to the enabling of ATO detection.
-
After you activate ATO detection, it may take about a week for the system to "learn" the users' behavior, and to then be able to produce more accurate alerts.
See also:
 See the available
See the available