This page includes:
About Cases
The Cases page lets you see a list of the Perception Point X‑Ray cases that have been opened in your organization. Cases are opened when:
-
A suspected ATO attempt is detected by Perception Point X‑Ray. For example, a suspicious mail inbox rule was set, or a suspicious login to a mail account was attempted. Some cases are added based on a combination of suspicious activities.
Note: Suspected ATO attempts are detected only if the Perception Point ATO functionality is enabled in the organization. The ATO functionality is available for Microsoft 365 installations only. For details, see Configuring Microsoft 365 - ATO detection.
-
An end-user downloads a significant number of files that contain sensitive data. For details, see Detecting sensitive file downloads.
Each new case is assigned the Open status. You can click any case in the Cases page to display additional details about the case, such as a description of the suspicious activity, and the user who performed the suspicious activity. You can analyze a case, and then resolve it, to remove it from the list of open cases.
The Perception Point IR Team constantly monitors all cases that are added. The Perception Point IR Team analyzes each case that is added, and determines if the suspicion is warranted - requiring further attention - or if the case can be closed. If the Perception Point IR Team determines that the case requires additional analysis by your organization, they will set the case stage to client. An email can also be sent to your organization, outlining the suspicions. The email will be sent to the recipients that are specified in the "Alert via email on malicious cases" setting. For details on configuring the email, see Configuring alerts.
The Cases page includes suspicious activity only. The Events page lists all events that have occurred in Perception Point X‑Ray - even if the events are not suspicious. For details, see Events.
To show the Cases page:
-
In Perception Point X‑Ray, in the left navigation menu, select Security Operations > Cases.
|
Any admin user with the "Self Analysis" role [or higher] can access the Cases page. |
Case severity
Perception Point X‑Ray assigns a severity to each case. You can modify the severity when you handle a case. [See Handling a case below.] The severity can be:
-
[
 ] Low: For example, a user logged-in.
] Low: For example, a user logged-in. -
[
 ] Medium: For example, Suspicious inbox rule change.
] Medium: For example, Suspicious inbox rule change. -
[
 ] High: For example, a user set up a mailbox rule that appears to be suspicious, such as "Suspicious Inbox Rule Detected".
] High: For example, a user set up a mailbox rule that appears to be suspicious, such as "Suspicious Inbox Rule Detected".
You can use the case severity to filter the cases shown in the Cases page.
![]()
Case status
Perception Point X‑Ray assigns a Malicious status to each new entry in the Cases page. After analysis, you can modify the status of the case. [See Handling a case below.]
-
[
 ] Clean: The case has been analyzed, and no suspicious activity was found.
] Clean: The case has been analyzed, and no suspicious activity was found. -
[
 ] Malicious: The case has been analyzed and malicious behavior was detected - or the case has not yet been fully analyzed, and the original Malicious status remains.
] Malicious: The case has been analyzed and malicious behavior was detected - or the case has not yet been fully analyzed, and the original Malicious status remains.
You can use the case status to filter the cases shown in the Cases page.
Case stage
Perception Point X‑Ray assigns a stage to each entry in the Cases page. The stage indicates where the case is in the analysis process. The status can be:
-
[
 ] Client: The case has been analyzed by the Perception Point IR Team. The Perception Point IR Team has assigned the case to your organization for further analysis.
] Client: The case has been analyzed by the Perception Point IR Team. The Perception Point IR Team has assigned the case to your organization for further analysis. -
[
 ] Closed: The case has been investigated and is now closed. No further analysis is required.
] Closed: The case has been investigated and is now closed. No further analysis is required.
You can use the case status to filter the cases shown in the Cases page.

Case triggers
The following are some of the triggers that will create new cases:
|
|
Suspected ATO cases |
Suspected download of sensitive data |
|---|---|---|
|
|
|
|
Handling a case
When you handle a case, you can change its status and severity. After you handle a case, the stage of the case will automatically be set to closed. After a case has been closed, you can't reopen the case.
|
Note: Only an admin user with the "Administrator" role can handle cases. |
To handle a case:
-
In the Cases page, locate the required case, expand its view, and then click the Handle Case [
 ] button on the right of the case.
] button on the right of the case.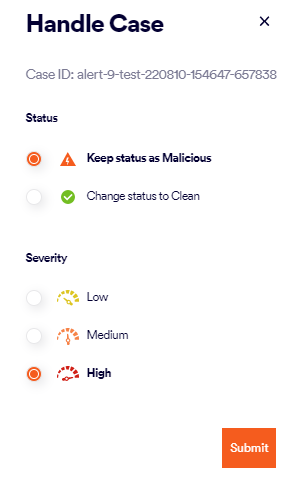
-
Set the Status and the Severity as required.
-
Click Submit.
UI elements
The Cases page includes the following UI elements:
|
UI element |
Description |
|---|---|
|
Stage |
See above. |
|
Severity |
See above. |
|
Status |
See above. |
|
Organization |
The organization in which the suspicious activity was detected. |
|
User |
The email account on which the suspected ATO activity was performed. |
|
Description |
A brief description of the suspicious activity. |
|
Timestamp |
The time and date on which the suspicious activity was performed. |
|
Handle case |
See above. |
Some of these UI elements appear - depending on the type of the suspicious activity that was detected:
|
Type of suspicious activity |
UI element |
Description |
|---|---|---|
|
IP Address |
The distribution of the IP addresses that have been used to sign-in to the targeted email account. |
|
Location |
The distribution of the locations [countries] from which users have signed-in to the targeted email account. |
|
|
Forward |
The email address to which the suspicious rule forwards emails. |
|
|
IP Address |
The distribution of the IP addresses that have been used to sign-in to the targeted email account. |
|
Location |
The distribution of the locations [countries] from which users have signed-in to the targeted email account. |
|
|
Operating System |
The distribution of the operating systems that have been used to sign-in to the targeted email account. |
|
|
Browser |
The distribution of the browsers that have been used to sign-in to the targeted email account. |
See also:
