This page includes:
About deploying the extension
Advanced Browser Security is deployed as a browser extension, adding advanced detection, DLP, and governance capabilities to standard browsers. This page will help you deploy and configure the extension, using the following 5-step procedure:
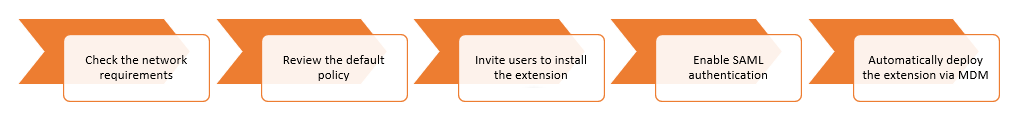

Step 1 - Check the network requirements
If your organization limits internet access [for example, by a firewall], you'll need to allow a set of domains to enable proper operation of the extension.
For details, see Networking requirements  .
.
Step 2 - Review the default policy
The recommended initial policy is to operate the extension in silent mode. In this mode, the extension will inspect every website and every file that is accessed from the browser - and report security events to the Advanced Browser Security console and to Perception Point X‑Ray.
Configuring policies
You use the Advanced Browser Security console to configure policies for the extension. This section describes how you can try out some common detection and DLP options, as described below:
Configuring detection settings
Detection settings are configured in the Detection Settings tab inside each policy.
To configure malicious file detection and malicious website options, follow these steps:
-
Sign-in to the Advanced Browser Security console.
-
Click Policies.
-
Click Default Policy.
-
Click the Detection Settings tab.
-
Under "File detection options" and "Website detection options" choose the required modes of operation.
-
Most evaluations start in Silent mode, in which events are reported to Perception Point X‑Ray - without notifying end-users.
-
If you want end-users to be warned or blocked when encountering a malicious website or a malicious file, choose either the Warn or the Block mode.
-
You can optionally set a custom message for users in the warn and block pages.
[More info: Detection Settings]
-
Configuring website rules
Website rules are configured in the Website rules tab inside each policy.
Follow these steps to configure a few sample website rules on sensitive websites:
-
Sign-in to the Advanced Browser Security console.
-
Click Policies.
-
Select the required policy, and then click the Website Rules tab.
-
Choose which of the following rules you want to add:
-
A rule that prevents users from accessing a specified domain.
-
A rule that prevents users from copying text out of a specified domain.
-
A rule that prevents users from printing from a specified domain.
-
A rule that prevents users from uploading files to a specified domain.
-
A rule that shows a watermark on all pages inside a specified domain.
-
Changes to these configurations will apply immediately. When users visit any of the websites configured above, they will be restricted as you configured. You can try these restrictions by trying to copy or print content, etc.
[More info: Website Rules]
Step 3 - Invite users to install the extension
If you're evaluating Advanced Browser Security, start by inviting specific end-users via email. When the end-users receive the email, they'll need to:
-
Click on the "Add extension" link in the email. The link will direct them to the extension in the correct extension store [Chrome Web Store, Edge Add-ons store, Mozilla Add-ons store, or Mac App Store] depending on the type of browser into which they are signed-in.
-
Add the extension to their browsers, and then sign-in to the extension with their work email addresses.
-
Receive a one-time verification code that is sent to their work email addresses.
-
Enter the verification code to complete the deployment and sign-in process. When the sign-in is successful, the extension will be activated.
[More info: Deploying the extension manually]
To send an email to invite users:
-
Sign-in to the Advanced Browser Security console - using your admin credentials.
(You should have received an admin invitation email with the details.)
-
Click Users, and then click Users.
-
Click Add new user.
-
Type the email addresses of your new users. Use any common delimiter to separate multiple addresses.
-
Select the policy that will be applied to the new users.
-
Select "Send email invitations asking users to install the extension"
-
Click Add users.
An invitation email will be sent to the addresses that you specified. Users can then open the email and follow the on-screen instructions to sign-in to the extension using their work email addresses. The sign-in process with activate the extension.
You can see which users have added the extension and signed-in, by clicking Users > Extensions in the Advanced Browser Security console.
The default policy will silently operate in the background to detect malicious websites that users access and malicious files that users download. These events will appear in the Scans page of Perception Point X‑Ray. In the Scans page, you can filter on the "Browser" channel [![]() ] to view events reported by the extension only.
] to view events reported by the extension only.
For organization-wide deployments, you can configure SAML authentication rather than adding users manually. [See Step 4 below]
|
Note: During a production deployment, users don’t need to manually sign-in to the Browser Extension - the extension can be centrally deployed and automatically activated for users. [More info: Organization tokens] |
Step 4 - Enable SAML authentication [Optional]
If your organization uses an identity provider - such as Microsoft Entra ID, Google Workspace, or Okta - you can configure SAML authentication, allowing the identity provider users to sign-in to the extension using their existing credentials. In this scenario, there is no need to add users to the Advanced Browser Security console.
For details on enabling SAML, see Identity Provider [IdP] Integration - SSO [ABS].
Note: To complete the organization-wide deployment, you'll need to deploy the extension via UEM. [see Step 5 below]
Step 5 - Automatically deploy the extension via UEM [Optional]
If your organization manages devices/ browsers via a UEM solution, you can use the UEM solution to automatically deploy the browser extension on all managed devices.
Once the extension is deployed on a user's browser, the user will be asked to sign-in with their work email address [or will be seamlessly signed-in if SAML authentication is configured].
For details on available deployment options for the extension, see Deploying the extension [Managed deployment].
See also: