This section includes:
About self analysis
You can use Perception Point X‑Ray to analyze a specific file or URL that is suspicious. This is called self-analysis. Perception Point X‑Ray will perform an analysis of the specified file or URL. Scan details are included in the Scans page in Perception Point X‑Ray. Remember to click the Self-analyze filter icon [ ] to show only Self-analyze scans.
] to show only Self-analyze scans.
If the file to be analyzed is password protected, you can supply the required password before scanning begins.
|
Note:
|
|
Any admin user with the "Self Analysis" role [or higher] can access the self-analysis feature. |
Self-analyzing a file or URL
Note: You can simultaneously upload multiple files for self-analysis.
To self-analyze a file or URL:
-
On the right of the Perception Point X‑Ray banner, click the Self Analyze icon [
 ].
].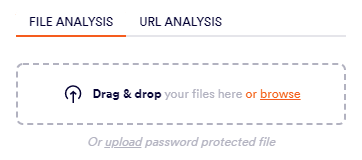
File Analysis
Regular files [not password-protected]
Password-protected files
-
Drag and drop the suspicious files, or browse to locate them.
-
Click upload to be able to enter the password.
-
Drag-and-drop the suspicious file, or browse to locate it.
-
Enter the password, and click Analyze.
Note: If you submit multiple files, the same password will be applied to all the files.
URL Analysis
-
Click URL Analysis.
-
Enter the suspicious URL, and then click Analyze.
-
-
Perception Point X‑Ray will analyze the files or URL. Results of the analysis will be shown. You can click any result to see additional details about the analysis.
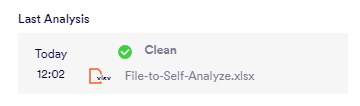
Important: It may take a while for the results of the scan to appear.
See also:
