Scan details structure
This section includes:
About scan details
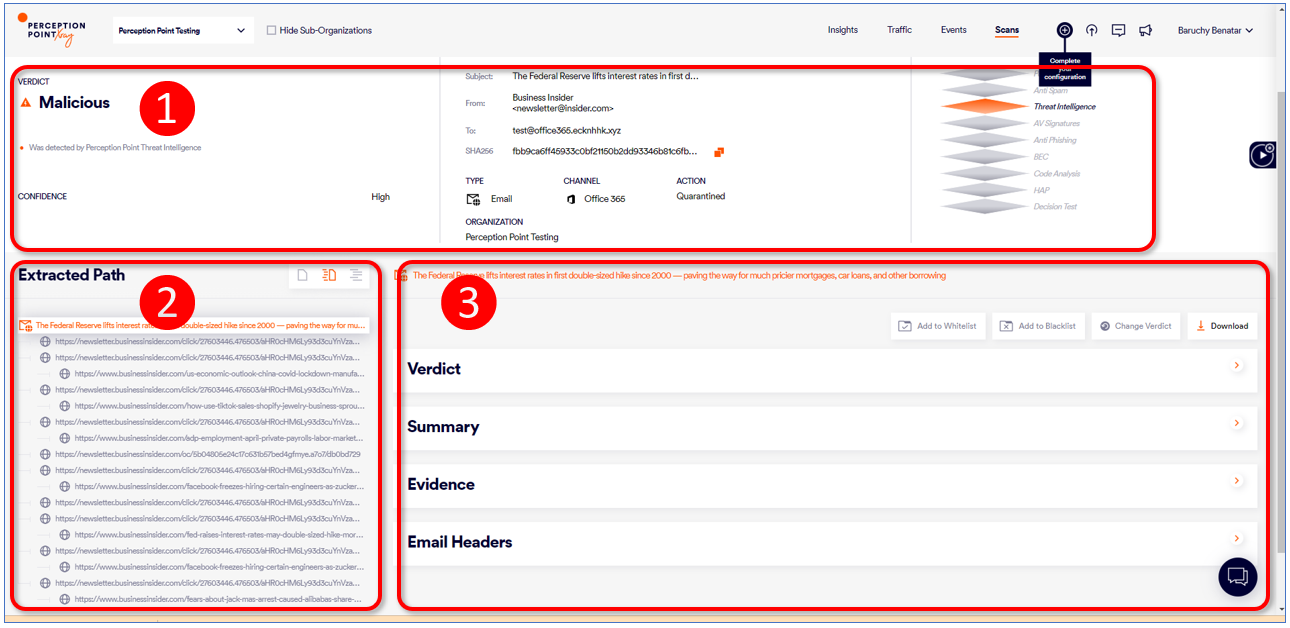
The Scans-details page lets you perform a detailed forensic analysis of any scan, allowing you to understand the high-level conclusion, as well as to quickly navigate to a malicious URL or a malicious file. The Scans-details page is split into the following three areas:
-
Scan overview
-
Attack path
-
Forensics
|
Any admin user with the "Self Analysis" role [or higher] can access the Scans-details page. |
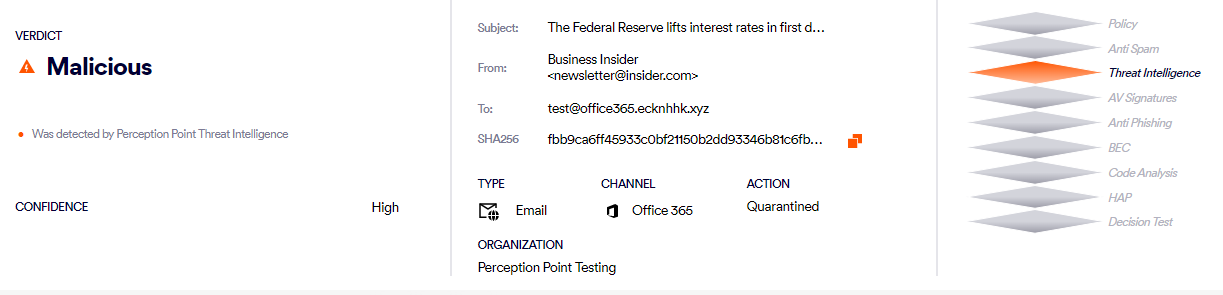
1. Scan overview
The top part of the Scans-details page contains a summarized view of the scan. It includes an aggregated view of the layers and engines that identified the incident, a preview (of the email), screenshots (of the web site), as well as highlights of the attack.
2. Attack path
Perception Point X‑Ray recursively unpacks every email, file, and URL, following almost every possible link to identify even hidden attacks. The left side of the Scans-details page allows you to easily navigate the unpacked tree and identify malicious nodes that are marked in orange. You can click on any orange malicious node to display additional forensics for that specific item.
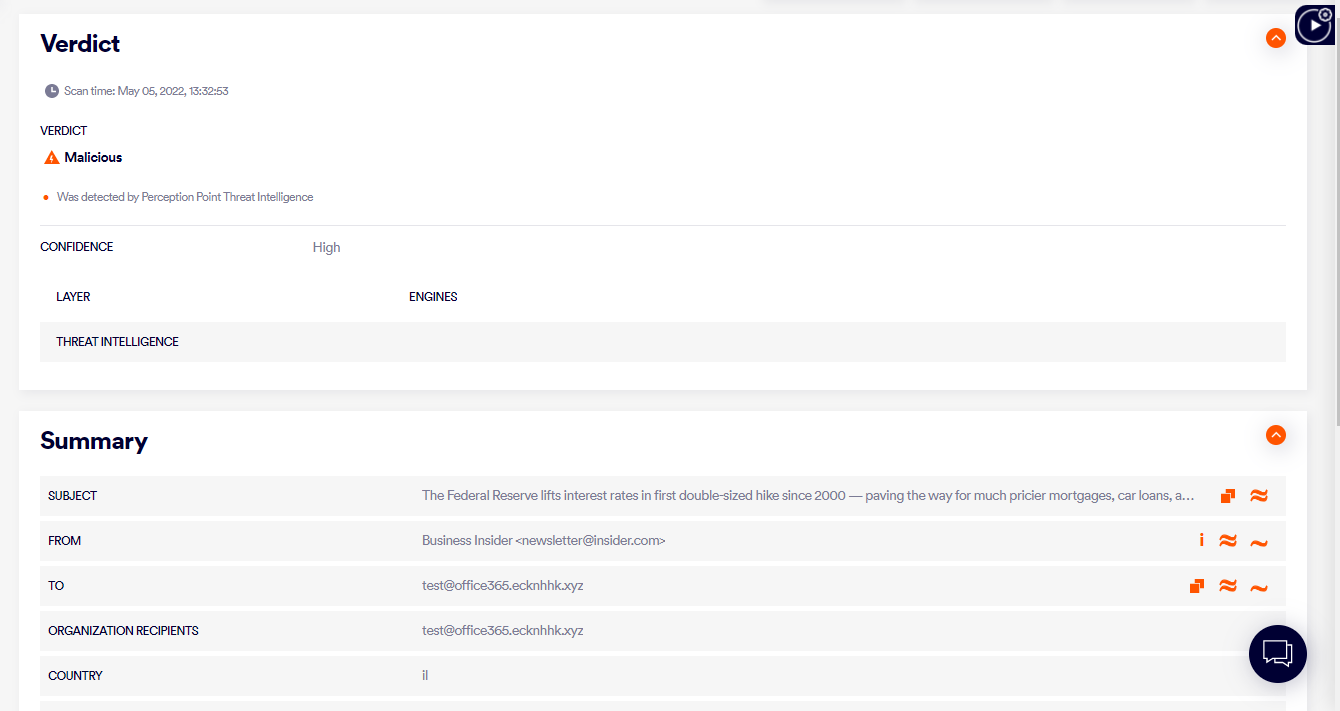
3. Forensics
You can click on any orange malicious node in the extracted path to display additional forensics for that specific node. Scans with a malicious verdict include an evidence section, detailing all the evidence that the system collected in order to determine that the scan is malicious. The scan details may also include exploit analysis, macro analysis, MITRE ATT&CK® mapping, and spawned processes.
See also: