This page includes:
About ATO cases
The Account Takeover page lets you see a list of the FortiMail Workspace Security ATO cases that have been opened in your organization. Each case represents a suspicion that a particular security occurrence has occurred within an email account in your organization. A case may be opened in scenarios when a suspected ATO attempt is detected by FortiMail Workspace Security. For example, a suspicious mail Inbox rule was set, or a suspicious login to an email account was attempted.
|
Note: Suspected ATO attempts are detected by FortiMail Workspace Security only if the ATO functionality is enabled for the organization. The ATO functionality is available for Microsoft 365 installations only [Inline and API]. For details, see Configuring Microsoft 365 - ATO detection. |
Typically, cases are added based on a combination of suspicious activities, that may originate in multiple integrated channels.
The Account Takeover page includes suspicious activity only. In contrast, the Events page lists all events that have occurred in FortiMail Workspace Security - even if the events are not suspicious. For details, see Events.
To show the Account Takeover page:
-
In FortiMail Workspace Security, in the left navigation menu, select Security Operations > Account Takeover.
|
Any admin user with the "Controller" role or the Administrator role can access the Account Takeover page. |
|
Note: The Account Takeover page and its functionality will be available only if a Microsoft 365 integration [Inline or API] is enabled for the organization. The ATO detection functionality is not available for Google Workspace, Microsoft Exchange, and "Other" integrations. |
Case alerts
Suspicious incidents that are detected in an email account, such as the creation of a suspicious mailbox rule, may create alerts. Alerts are the building blocks of every case. Each case can include one-or-more alerts. By including multiple alerts in a case, the comprehensiveness of the case is enhanced - making the case easier to review, analyze, and resolve. When an alert is created, a new case may be opened. More significant alerts - known as trigger alerts - are able to open a new case. Every case will have one-or-more trigger alerts. Less significant alerts may be insufficient to open a new case.
After a case has been opened [and remains open], as additional alerts are created, they are added to the case. When a case has the Closed status, new alerts are no longer added to the case. Instead, when necessary, a new case will be opened, and the new alerts will be added to the new case.
Some alerts may include one or more events.
The following are some of the alerts that may be included in a case:
|
ATO Remediation
|
Important: See Enabling the ATO-case remediation functionality below. |
Each ATO case in FortiMail Workspace Security includes remediation functionality. The remediation functionality is a list of recommended actions that should be performed to help remediate the ATO case. The set of recommended remediation actions is tailored to each specific case. After selecting a case in the Account Takeover Cases page, you can click the Remediate button to display the recommended remediation actions.
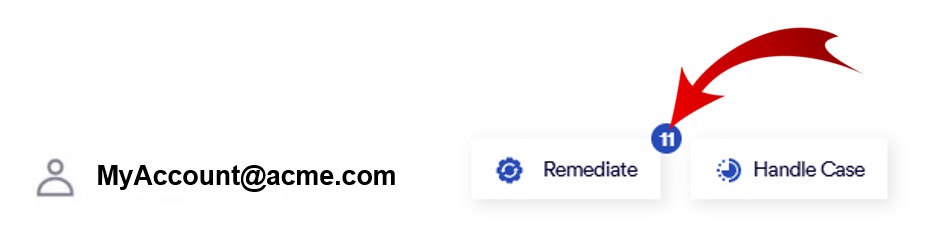
-
The round-blue badge on top of the Remediate button indicates the total number of remediation actions that are recommended for the case.
-
When you click the Remediate button, the "Account Remediation and Recovery steps" pane opens. This pane shows the list of recommended remedial actions for the selected case.
-
For the remediation to be most effective, it is recommended to perform the recommended actions in the same order in which they appear in the list.
-
It is possible to automate some of the recommended actions. For details, see Configuring automatic remediation below.
Each recommended remedial action can be in one of three states. These states help to track the performance of the recommended actions:
|
State |
Description |
|
|---|---|---|
|
Pending |
|
Each recommended action begins in the Pending state - unless it was performed automatically when the case was created. The Pending state indicates that the action must still be acted upon. Each Pending action can be:
|
|
Complete/Done |
|
The recommended action has been performed - either automatically, or using any of the three methods listed above. |
|
Ignore |
|
An admin-user clicked Ignore, to indicate that there is no need to perform the recommended action in the current scenario. |
Action Types
|
Confirmation |
It is possible to verify and confirm that the end-user is familiar with the specified action. For example, did the end-user perform the suspicious change to an Inbox rule, or did the user sign-in from a suspicious location? Only manual confirmation is possible. |
|
|
Mitigation |
Mitigating the user’s account takeover status by performing any of the following procedures:
All the above mitigation procedures can be performed either manually or via the Microsoft 365 integration. Typically, they should be performed in the order shown above.
|
|
Note: Some of the actions shown above can be reverted [manually or via Microsoft 365] using the controls that are available in the ATO Cases UI. |
When each of the recommended actions is in either the Complete state or the Ignore state, then the "Resolve Case" section appears.
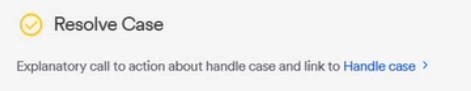
The "Resolve Case" section includes a link to the "Handle Case" functionality. For details, see Handling cases - the process below.
Configuring automatic remediation
You can configure various recommended remedial actions that will be performed automatically - via Microsoft 365 - when a case is created.
|
Remedial action |
Details |
|
|---|---|---|
|
Disable user (Block user ability to connect) |
Scenario A new case is created, and the case is assigned a High severity. The case includes a recommended remedial action to disable [lock] the user's account. Automated action The user's account will be automatically locked via Microsoft 365 - when the case is created. The recommended action will have the Done state.
|
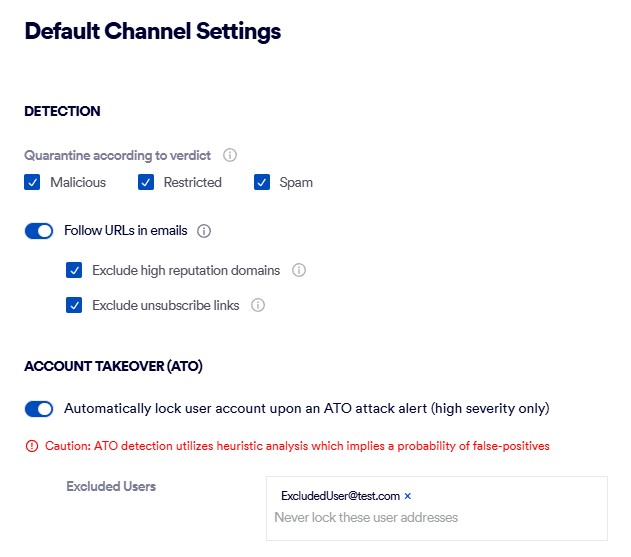
To configure automatic remediation:
-
Navigate to Settings > "Bundles and Channels".
-
Scroll down to the "Enabled Channels" section.
-
Click "Default Channel Settings" - in the top-right corner.
-
In the Default Channel Settings pane, click Edit.
-
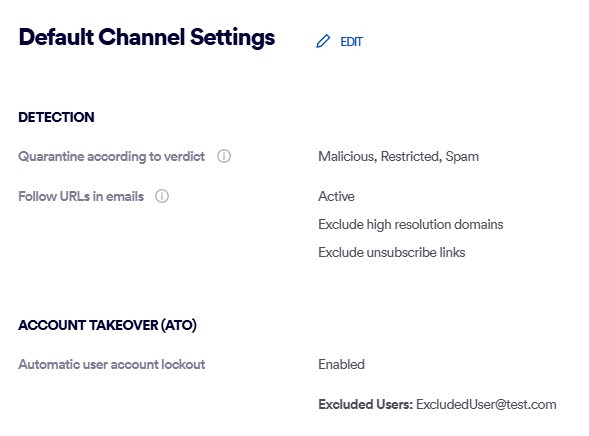
Under "Account Takeover (ATO)", enable "Automatically lock user account upon an ATO attack alert (high severity only)"
-
Under Excluded Users, specify the email addresses of any accounts that should be excluded from the automated account locking functionality.
-
Click Save.
Enabling the ATO-case remediation functionality
To access the full ATO Remediation functionality, it may be necessary to request additional Microsoft 365 permissions:
-
For organizations that on-boarded their Microsoft 365 integration after 22 December 2025, the ATO-case remediation functionality will be automatically available - it is not necessary to perform the procedure shown below.
-
For organizations that on-boarded their Microsoft 365 integration before 22 December 2025, perform the procedure shown below in order to enable the full ATO-case remediation functionality.
Enabling the ATO-case remediation functionality
The procedure below will refresh the requested permissions that are associated with the Perception Point ATO remediation app - in order to grant additional permissions to the remediation app.
-
Sign-in to the Microsoft 365 admin center.
-
In the left navigation menu, select Admin centers > Identity.
-
In the left navigation menu, select Applications > Enterprise applications.
-
Click "Search by application name or object ID"
-
In the list of applications, locate and then select "Perception Point (ATO App)".
-
Under Security, click Permissions.
-
Select "Grant admin consent for <your Microsoft Account>".
-
If required, select your Microsoft account.
A list of the "Permissions requested" will be displayed.
-
Click Accept.
|
Note: After you perform the above procedure, it may take up to 1 hour for the additional permissions to be granted, and for the ATO-case remediation functionality to be functional. |
These are the new permissions that will be added:
-
User.RevokeSessions.All
-
User.ManageIdentities.All
-
UserAuthenticationMethod.ReadWrite.All
-
User.EnableDisableAccount.All
Handling cases - the process
Each entry in the Account Takeover page has a status - Open, Under investigation, or Closed. The status indicates where the case is in the investigation process. Use the "case handling" process described below to make sure that all cases are either in the Closed status, or are progressing towards the Closed status.
Each new case is assigned the Open status. You can configure FortiMail Workspace Security to send an email alert each time a new case is opened. [For details, see Sending email alerts [notifications] below.] When you receive an email alert, use the available filters to locate the new case in the Account Takeover page, review the information that is displayed, and then begin to handle the case [as described below].
If a case includes any changes to its status, then a Case History button will appear. Use this button to display a summary of the changes that have been made to the status of the case.
For any case in the Account Takeover page, you can click Handle Case [![]() ] to proceed with the investigation process, as follows:
] to proceed with the investigation process, as follows:
|
Current Status |
Click "Handle Case" to: |
|---|---|
|
[ |
Request an investigationReason: You aren't sure if the case is a true positive [TP] or a false positive [FP], and you want the FortiMail Workspace Security IR Team to investigate the case.
Close the caseReason: You are sure that the case is either:
You'll need to specify the case accuracy:
The case status will change to Closed. |
|
[ |
No Handle Case functionality is available. The case is waiting for the FortiMail Workspace Security IR Team to complete their investigation. The FortiMail Workspace Security IR Team will either:
|
|
[ |
Re-open the caseReason: You have reviewed the case history, and now you want to indicate that you think that the case is a true positive [TP] or a false positive [FP].
Request an investigationReason: You have reviewed the case history, and now you want the FortiMail Workspace Security IR Team to [re]investigate the case.
|
Sending email alerts [notifications]
You can configure FortiMail Workspace Security to send an email alert [notification] each time a new case is opened. The alert is sent to one-or-more admin users. For details, see Alert via email on malicious cases. When you receive an email alert, use the available filters in the Account Takeover page to locate the new case. Review the information that is displayed, and then begin to handle the case, as described in Handling cases - the process above.
|
Note: Email alerts are not sent to end-users - they are sent to admin users only. |
Existing ATO cases
Email alerts are sent only when a new ATO case is opened. When additional suspicious activity [such as an alert or an event] is added to an open ATO case, an email alert is NOT sent.
After an ATO case is closed, if suspicious activity is then detected for the same user, a new case will be triggered [opened] and an email alert will be sent.
|
Transitioning to the new Account Takeover page On 8 July 2025, the existing Cases page in FortiMail Workspace Security was replaced by the new Account Takeover page. All cases from the Cases page were transferred to the new Account Takeover page. Email alerts for these cases were originally sent out when the cases were first opened in the Cases page. When additional suspicious activity [such as an alert or an event] is first added to one of these "transferred" cases in the new Account Takeover page, a new email alert will be sent. This email alert will refer to the original date on which the case was first opened in the Cases page, but will redirect to the new Account Takeover page. After this additional email alert is sent, no further email alerts will be sent for this case. Use the "case handling" process described above to handle the case as required. |
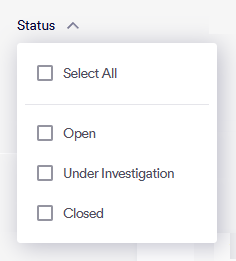
Case status
Each entry in the Account Takeover page has a status. The status indicates where the case is in the investigation process. The status can be any of the following:
|
Open |
The case has been opened. It has not yet been investigated by the FortiMail Workspace Security IR Team. The FortiMail Workspace Security IR Team won't investigate the case while it has the Open status. |
|
Under Investigation |
The case is being investigated by the FortiMail Workspace Security IR Team. |
|
Closed |
The case is now closed. No further investigation into the case will be performed - unless the case is re-opened. |
You can click Handle Case [![]() ] to change the status of a case. For details, see Handling cases - the process above.
] to change the status of a case. For details, see Handling cases - the process above.
You can use the case Status to filter the cases that are shown in the Account Takeover page.
Case severity
FortiMail Workspace Security assigns a severity to each case when the case is created. The severity of each case is based on the alerts that are included in the case. You can't modify the severity of a case. The severity can be:
-
Low: For example, a user logged-in.
-
Medium: For example, "Suspicious Inbox rule was detected".
-
High: For example, a user set up a mailbox rule that appears to be suspicious, such as "Suspicious Inbox rule created".
You can use the case Severity to filter the cases that are shown in the Account Takeover page.

See also:



 ] Open
] Open ] Under Investigation
] Under Investigation ] Closed
] Closed