This page includes:
About managing endpoint users
The Users > Users page in the Advanced Browser Security console lets you add and manage the endpoint users in your organization. Endpoint users have the extension added to browsers on their computers.
In the Users > Users page, you can click any user in the list to see details about the user. The details are shown in the following tabs:
-
The General tab shows additional details about the user. It also shows a list of all the ABS browser extensions that the user has installed. Multiple entries will exist when a user has added the extension to multiple browser profiles.
-
The Extension Activity tab shows the various tasks that were performed inside the browser with the extension - for that particular user.
-
The Policy assignment rule tab shows the attributes that are set for the user, and the rule that was used to assign the policy to the user. This tab is available only if the user is an IdP user, not a local Perception Point user. For details, see User SAML attributes and assigned policies.
Adding new endpoint users
The process for adding new Perception Point users differs slightly - depending on where the user credentials are maintained:
-
Local Perception Point users: If the Perception Point user credentials are managed using the Advanced Browser Security console, then you use the Users > Users page to add new endpoint users. When you add new users, you specify the policy that will be assigned to the new users.
-
IdP users: If the Perception Point user credentials are managed by an external identity provider - such as Microsoft Entra ID or Okta - then it is not necessary to use the Advanced Browser Security console to add new users. Instead, all users that are registered in the external identity provider will have access to the extension - it is not necessary to add users in the Advanced Browser Security console.
More information
-
Before adding a new user, make sure that the user's computer meets the system requirements. For details, see Installation requirements
See also
-
For details on policies, see Policies.
To add new endpoint users using the Advanced Browser Security console:
-
Open the Advanced Browser Security console, and navigate to the Users > Users page.
-
Click Add new user.
-
Enter the email addresses of the new users.
You can enter multiple email addresses. Use any common delimiter to separate multiple addresses. -
Select the policy that will be applied to the new users.
-
[Optional] Select the Send email invitations asking users to install the extension check box if you want to send an invitation email to the new users.
-
Click Add users.
The system adds the new users. The new users have the Invited status.
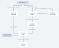
Understanding user status
Each end user in the Advanced Browser Security console can have one of the statuses below:
|
Status |
Description | Method used to add the user |
|---|---|---|
|
Invited |
An email invite was sent to the user from the Advanced Browser Security console, but the user has not yet clicked the "Add Extension" button in the email. |
|
|
Clicked invite |
An email invite was sent to the user from the Advanced Browser Security console, and the user has clicked the "Add Extension" button in the email. The user has not yet signed-in to activate the extension. |
|
|
Pending login |
The user is available in the system [an invitation email was not sent], but the user has never signed-in to the extension. |
|
|
Active |
The user has signed-in to activate the extension. The user is currently active - or has been active during the previous hour. |
|
|
Inactive |
The user has signed-in to activate the extension. The user isn’t currently active - and wasn't active during the previous hour. |
|
|
Invitation failed |
An invitation email was sent to the user, but the invitation email bounced or another complaint was received by Perception Point. |
|
Flowchart of user status...
Deleting endpoint users
When an endpoint user is no longer required, you can delete the user from the Advanced Browser Security console. When you delete a user, the user will be logged-out of the extension, and will no longer have access to the extension.
|
Note The log-out process may take up to an hour to perform, and will occur only if the user has internet access. |
To delete an endpoint user:
-
Open the Advanced Browser Security console > Users page, and click Users.
-
Select the user or users that you want to delete.
-
Click Actions > Delete user or Delete x users. The "Delete users" dialog box appears.
-
Click "Yes, delete users"
Manually assigning a policy to existing endpoint users
When endpoint users are created, they are assigned policies. You can change the policy that is assigned to existing endpoint users.
-
If the user is a local Perception Point user, then the newly assigned policy will remain assigned to the user - until it is manually changed.
-
If the user is an IdP user, then the newly assigned policy will override the policy that was previously assigned based on assignment rules. The newly assigned policy will remain assigned to the user - either until the policy is manually changed, or until the policy override is cleared. After the policy override is cleared, the assigned policy will be determined by the policy assignment rules. For details about using rules to assign policies, see Using rules to assign policies.
Note
If the policy for an IdP user is overridden, in the Users page the policy will appear with an i-icon [
 ] indicating that the policy has been overridden.
] indicating that the policy has been overridden.
To assign a policy to existing endpoint users:
-
Open the Advanced Browser Security console > Users > Users page.
-
Select the users [
 ] to which you want to assign a policy.
] to which you want to assign a policy. -
Click Actions > Assign policy and then select the required policy.
-
Click Assign.
To clear a policy override for endpoint users:
-
Open the Advanced Browser Security console > Users > Users page.
-
Locate and select the users [
 ] for which you want to clear the policy overrides. An i-icon [
] for which you want to clear the policy overrides. An i-icon [ ] indicates that the policy has been overridden.
] indicates that the policy has been overridden. -
Click Actions > Clear policy override. The policy overrides are cleared, and the policy assignment rules are applied to the users.
See also: