|
Note:
|
This page includes:
About deployment via GPOs in Active Directory
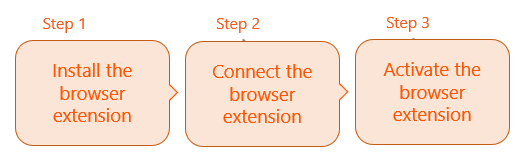
If you are using GPOs in Active Directory to manage your Windows devices, then you can use GPOs to deploy the browser extension. The deployment process includes the three standard ABS extension deployment steps.
|
Important: Make sure to see additional important details on the 3-step deployment process, Deploying the extension [Managed deployment]. |
This page shows specific GPO details for Step 1 and Step 2 of the deployment process.
Step 1: Install the browser extension
|
Important: Before your perform Step 1, make sure to see additional important details: Step 1: Installing the extension via UEM solutions [Generic]. |
You can use GPOs to deploy the browser extension on Windows devices.
Below is a summarized procedure of Step 1, using a GPO to install the browser extension. You'll need to perform this procedure for each browser (Google Chrome, Microsoft Edge, Firefox). Further details for each browser are shown below.
-
Go to each browser’s support portal to get the required ADM(X) template file.
-
Open the ADM(X) file using the Group Policy Editor [gpedit.msc].
-
Configure the browser policy to force-install the browser extension.
Instructions for Google Chrome
-
Open the official Google Chrome instructions
 :
: -
In the instructions, scroll down to "Install and configure Chrome policy templates" and then click Windows.
-
Perform "Step 1: Download Chrome policy templates".
-
Perform "Step 2: Open the ADM or ADMX template you downloaded".
-
Scroll down to "Step 3: Configure policies".
-
In the GPO Editor, open the template you just added and change the following configuration settings:
-
Navigate to Computer Configuration > Administrative Templates > Classic Administrative Templates (ADM) > Google > Google Chrome > Extensions, and open Extension management settings.
-
Enable the setting - if it is not already enabled.
-
If the value is empty or just {}, set the value to the following:
{"kpehlcnleoaejbmmgncofcgpjnojlfbn":{"installation_mode":"force_installed","toolbar_pin":"force_pinned","update_url":"https://clients2.google.com/service/update2/crx"}}
Otherwise, if there was a previous value in the format {<something>}, edit the value to be like this:
{<something>,"kpehlcnleoaejbmmgncofcgpjnojlfbn":{"installation_mode":"force_installed","toolbar_pin":"force_pinned","update_url":"https://clients2.google.com/service/update2/crx"}}
-
Instructions for Microsoft Edge
-
Open the official Microsoft Edge instructions
 :
: [https://learn.microsoft.com/en-us/deployedge/configure-microsoft-edge]
-
In the instructions, perform "1. Download and install the Microsoft Edge administrative template".
-
Perform "2. Set mandatory or recommended policies".
-
In the GPO Editor:
-
Navigate to Computer Configuration > Policies > Administrative Templates > Classic Administrative Templates (ADM) > Microsoft Edge > Extensions, and open Extension management settings.
-
Enable the setting - if it is not already enabled.
-
If the value is empty or just {}, set the value to the following:
{"jcllaekmhcebhkjmmlnbcdmbbpiidnhf":{"installation_mode":"force_installed","toolbar_state":"force_shown","update_url":"https://edge.microsoft.com/extensionwebstorebase/v1/crx"}}
Otherwise, if there was a previous value in the format {<something>}, edit the value to be like this:
{<something>,"jcllaekmhcebhkjmmlnbcdmbbpiidnhf":{"installation_mode":"force_installed","toolbar_state":"force_shown","update_url":"https://edge.microsoft.com/extensionwebstorebase/v1/crx"}}
-
-
Perform "3. Test your policies".
Instructions for Firefox
-
Follow the official Firefox instructions
 :
: [https://support.mozilla.org/en-US/kb/customizing-firefox-using-group-policy-windowse]
-
In the GPO Editor, edit the ExtensionSettings setting:
-
If the value is empty or just {}, set the value to the following:
{"advancedbrowsersecurityaddon@perception-point.io":{"default_area":"navbar","install_url":"https://addons.mozilla.org/firefox/downloads/latest/advanced-browser-security/latest.xpi","installation_mode":"force_installed"}}
Otherwise, if there was a previous value in the format {<something>}, edit the value to be like this:
{<something>}, edit the value to be like this {<something,"advancedbrowsersecurityaddon@perception-point.io":{"default_area":"navbar","install_url":"https://addons.mozilla.org/firefox/downloads/latest/advanced-browser-security/latest.xpi","installation_mode":"force_installed"}}
-
Step 2: Connect the browser extension
|
Important: Before your perform Step 2, make sure to see Step 2: Connecting the extension via UEM solutions [Generic]. |
Step 2 includes the following two sub-steps:
|
Step 2 Connect the browser extension
|
Step 2A |
Get the PowerShell script You can download a PowerShell script that contains the required organization token - from the Advanced Browser Security console.
|
|
Step 2B |
Deploy the PowerShell script Use a GPO in Active Directory, or any other tool, to push the downloaded PowerShell script file [that you downloaded in Step 2A above] to all relevant Windows devices. This will deploy the organization token on the target devices. |
Step 3: Activate the browser extension
For details on Step 3, see Step 3: Activating the extension on endpoints.
See also: