|
Note: Conditional access is not available for Safari and Firefox. |
This page includes:
About conditional access integration
You can ensure that users can access specific work-related web apps only when both of the following conditions are in place:
-
The extension is installed on the browser that is used to access the specific web app.
-
The user is signed-in to the extension.
This conditional access functionality is particularly useful for unmanaged devices, to prevent users from accessing specific sensitive cloud apps from unprotected browsers.
To implement this functionality, you'll need to provide the hostnames of your identity provider's login pages.
|
Note: When the conditional access feature is enabled:
|
|
Important: Before you uninstall the extension, make sure to disable conditional access for all apps. |
Configuring conditional access integration
Below is a generic procedure for configuring conditional access integration. There are also customized procedures for the following identity providers:
Configuring conditional access [Generic]
To ensure that users access work-related web apps only from a browser that has the extension installed:
-
In your identity provider, open the conditional access web application integration settings.
-
Add a Source IP condition - that includes the IP ranges below:
IP ranges
-
3.24.49.69/32
-
52.48.99.246/32
-
54.236.214.198/32
-
-
-
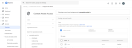
In the Advanced Browser Security console, open the relevant policy. [See Policies]
-
Open the "Conditional Access" tab.
-
Under Proxy login requests > Login hostnames, add the hostnames of your identity provider's login pages, such as login.microsoftonline.com or accounts.google.com.
-
Enable the Proxy login requests toggle and save the policy.
-
-
Test to make sure that users can access the sensitive web apps only when the extension is installed, and the users are signed-in to the extension.
Configuring conditional access [Entra ID]
-
In Entra Portal, open the Conditional Access settings.
-
In "Named locations", add a new trusted IP ranges location named "Perception Point Advanced Browser Security Proxy", with these IP ranges:
IP ranges
-
3.24.49.69/32
-
52.48.99.246/32
-
54.236.214.198/32
-
-
In "Policies", add or edit the relevant policy to include a Source condition - with the new named location as the source.
-
-
In the Advanced Browser Security console, open the relevant policy. [See Policies]
-
Open the "Conditional Access" tab.
-
Under Proxy login requests > Login hostnames, add login.microsoftonline.com as the login hostname.
-
Enable the Proxy login requests toggle and save the policy.
-
-
Test to make sure that users can access the sensitive web apps only when the extension is installed, and the users are signed-in to the extension.
Configuring conditional access [Google Workspace]
|
Limitations:
|
When you integrate with Google Workspace as the identity provider, to enable the conditional access feature to function, perform the following procedure:
-
In the Google Workspace Admin Console, go to Security > "Access and data control" > "Context-Aware Access"
-
Click the Basic tab.
-
Create an access level with a device policy that requires the following condition:
After "If you'll be adding more than 1 condition, select how all conditions are joined", select AND.
Under "Condition 1", after "Apply condition if users," select "Meet attributes"
Add one condition: "IP subnet" "Is" <IP subnet: Enter the set of IP ranges below:>
IP ranges
3.24.49.69/32
52.48.99.246/32
54.236.214.198/32
-
Continue under "Context-Aware Access", and assign this new access level to the required organizational unit and to the required sensitive apps.
-
In the Advanced Browser Security console, open the relevant policy. [See Policies]
-
Open the "Conditional Access" tab.
-
Under Proxy login requests > Login hostnames, add accounts.google.com as the login hostname.
-
Enable the Proxy login requests toggle and save the policy.
-
-
Test to make sure that users can access the sensitive web apps only when the extension is installed, and the users are signed-in to the extension.
Configuring conditional access [Okta]
-
Open the Okta Admin Console of your organization.
-
In Security > Networks, add a new IP zone named "Perception Point Advanced Browser Security Proxy", with the IP ranges below as the Gateway IPs.
IP ranges
-
3.24.49.69/32
-
52.48.99.246/32
-
54.236.214.198/32
-
-
Go to Applications > Applications. For each web application that needs conditional access, open the web application settings. In "Sign On", add or edit a Sign On Policy to have the Location set to the IP zone added above.
-
-
In the Advanced Browser Security console, open the relevant policy. [See Policies]
-
Open the "Conditional Access" tab.
-
Under Proxy login requests > Login hostnames, add the Okta organization hostname (for example acme.okta.com) as the login hostname.
-
Enable the Proxy login requests toggle and save the policy.
-
-
Test to make sure that users can access the sensitive web apps only when the extension is installed, and the users are signed-in to the extension.
See also: