This section includes:
|
Note: Before implementing this channel integration, contact your Customer Success Manager for FortiMail Workspace Security to make sure that this functionality is included in your current FortiMail Workspace Security license. |
About the FortiMail Workspace Security-SentinelOne integration
FortiMail Workspace Security can be integrated with various products. This page explains the configurations that are required to integrate FortiMail Workspace Security with SentinelOne. This page describes what must be performed by FortiMail Workspace Security Support and what must be performed by you, a FortiMail Workspace Security admin-user, to perform the integration.
When FortiMail Workspace Security is integrated with SentinelOne, information is shared between FortiMail Workspace Security and SentinelOne. This enables both FortiMail Workspace Security and SentinelOne to improve the security that they provide in your organization.
From SentinelOne to FortiMail Workspace Security
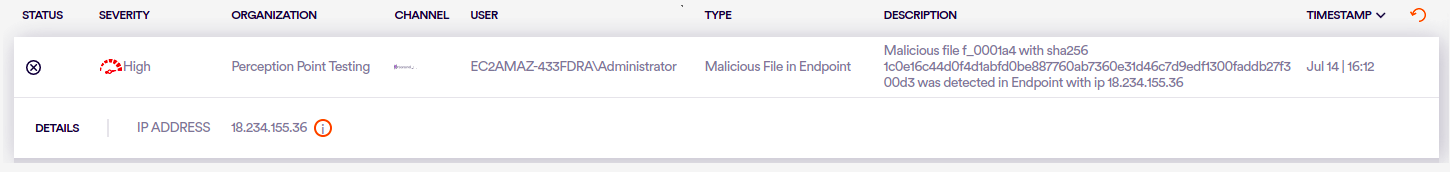
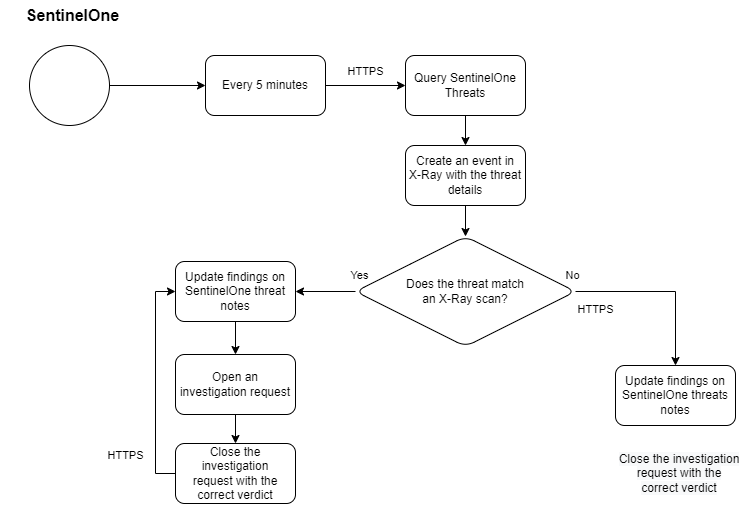
SentinelOne will periodically send to your FortiMail Workspace Security installation a list of all files that were detected by SentinelOne to be malicious, in your organization. The hash of each of the malicious files is also sent. FortiMail Workspace Security will use this information to improve its scanning accuracy within your organization.
-
For each malicious file detected by SentinelOne, an event is added to the FortiMail Workspace Security event log. Each event in the log is assigned a high severity, and has the "Malicious File in Endpoint" type. This enables you to monitor the malicious events that are detected by SentinelOne - and shared with FortiMail Workspace Security. For details, see Events.
-
If a malicious file detected by SentinelOne has been included in a FortiMail Workspace Security scan [based on the hash value of the file], a note will be added to the scan details in FortiMail Workspace Security, indicating that SentinelOne found the file to be malicious. A request will be automatically generated to the FortiMail Workspace Security IR Team to investigate the file.
From FortiMail Workspace Security to SentinelOne
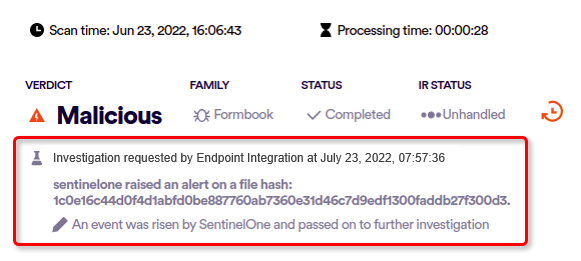
For each malicious file that FortiMail Workspace Security was informed about by SentinelOne, FortiMail Workspace Security creates a note in the Incidents > Threats page in SentinelOne.
The notes indicate:
-
Did FortiMail Workspace Security scan the file?
-
If the file was scanned by FortiMail Workspace Security, what scan verdict did FortiMail Workspace Security originally assign to the file.
-
What verdict did FortiMail Workspace Security assign to the file after analysis by the FortiMail Workspace Security IR Team?
|
Note: Malicious files that are detected in SentinelOne are included in the Events page in FortiMail Workspace Security. For details, see Events. |
The SentinelOne integration procedure
Perform the 3-step procedure below to integrate FortiMail Workspace Security with SentinelOne.
|
Steps |
|---|
|
Step 1 - Enabling and configuring FortiMail Workspace Security |
|
Step 2 - Configuring SentinelOne |
|
Step 3 - Verifying the integration |
Step 1: Activating and configuring the FortiMail Workspace Security-SentinelOne integration
This step activates and configures the FortiMail Workspace Security-SentinelOne integration in FortiMail Workspace Security.
In FortiMail Workspace Security
-
In FortiMail Workspace Security, in the left navigation menu, select Settings > Bundles and Channels.
-
Under Assigned Bundles, make sure that at least one bundle is assigned that includes the SentinelOne channel.
Note:
-
If a bundle that includes the SentinelOne channel is assigned, then SentinelOne will appear in the list of channels under Enabled Channels.
-
You can click Bundles Settings, that is located on the right of each Assigned Bundle, to see which channels are included in a bundle.
-
-
Under Enabled Channels, locate "SentinelOne" and then click "Activate" located on the right.
The Granting Access dialog box opens.
Note: If the Activate button does not appear, SentinelOne may not have been successfully enabled by FortiMail Workspace Security Support. Contact FortiMail Workspace Security Support [support@perception-point.io] for assistance.
-
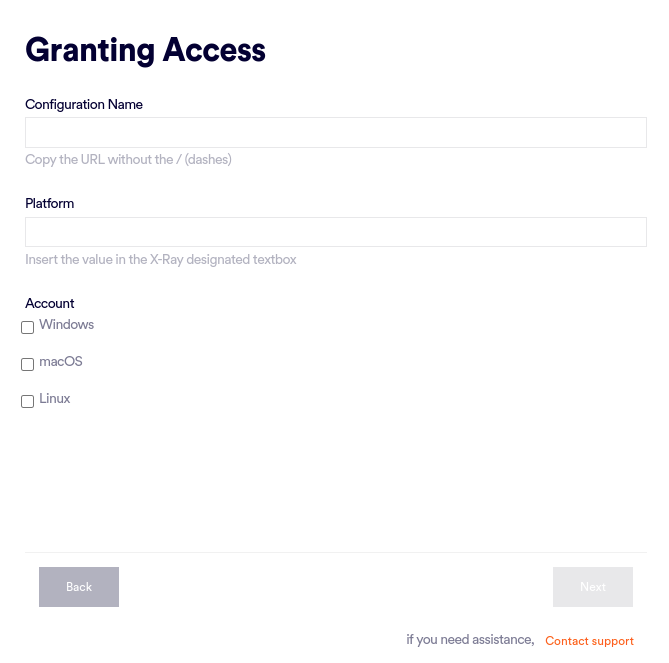
Enter the required information, described below:
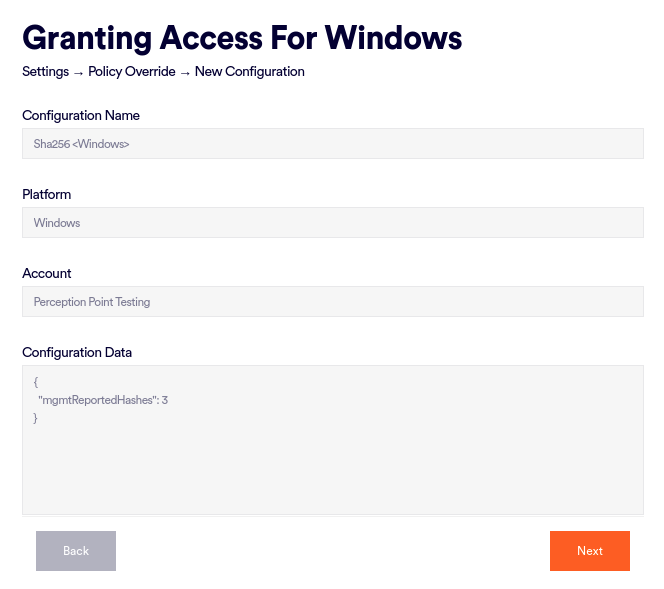
Configuration name
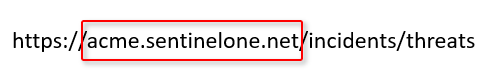
Enter your SentinelOne configuration name. Your SentinelOne configuration name is the text after https://, and ending with sentinelone.net, in your SentinelOne URL.
In the example below, the SentinelOne configuration name would be acme.sentinelone.net
Platform
[API Token]
Insert the SentinelOne API token.
To get the required API token:
-
In the SentinelOne Management Console, click Settings in the left panel.
-
Click Users in the top bar.
-
Create a new user [click New User], or select an existing user.
Note:
-
The user must be a "console" user - and not a "service" user.
-
The user must have the "Admin" role.
-
-
Click Generate API token [or regenerate the token].
-
When the API token appears, click Copy.
-
Paste the token into the Platform field in FortiMail Workspace Security.
Note: Although the SentinelOne API token may be valid for only 30 days, the token will be automatically renewed before the period ends.
Account
Select all the endpoint operating systems (platforms) [Windows / Mac / Linux] that will be included in the FortiMail Workspace Security-SentinelOne integration. Each of the selected platforms will require its own configuration.
-
-
Click "Next".
The Granting Access for Windows/Linux/macOS dialog box opens. [The dialog boxes that appear depend on the platforms that you specified in Account above.]
You'll now need to copy this information from FortiMail Workspace Security into SentinelOne, as described in Step 2 below.
Step 2: Configuring SentinelOne
This step configures the FortiMail Workspace Security-SentinelOne integration in SentinelOne.
-
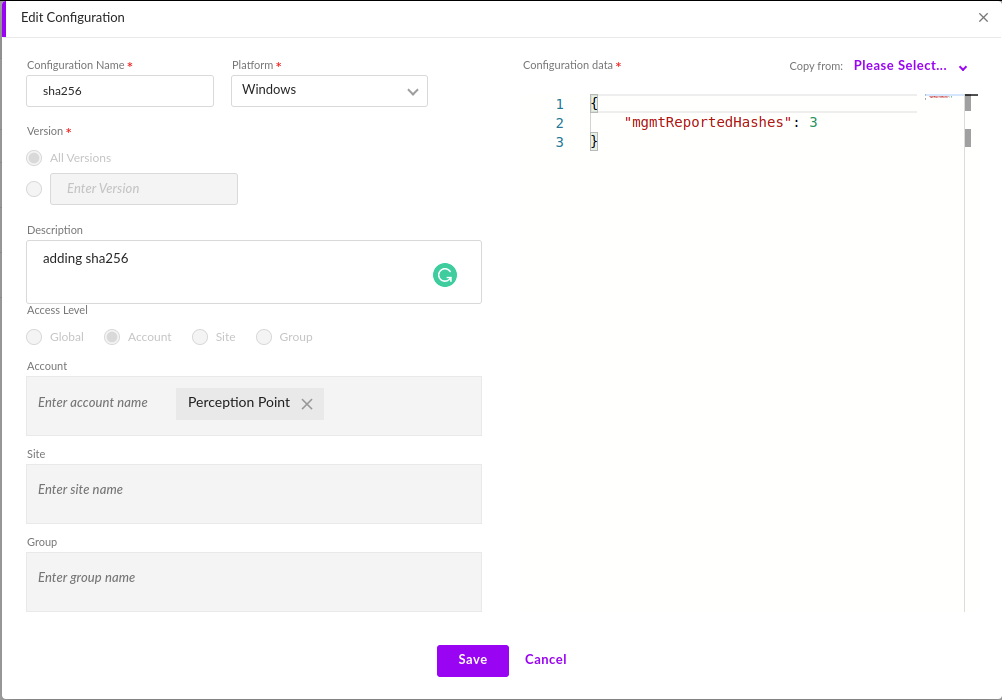
In the SentinelOne Management Console, select Settings > Policy Override.
Important: In the Policy Override, you can have only a single configuration for each operating system type (platform) [Windows / Mac / Linux]. If a configuration already exists in the Policy Override for any of the operating systems, in the step below, don't create a new configuration for that operating system, but rather modify [edit] the existing configuration.
-
For each platform [Windows / Mac / Linux]:
-
Click New Configuration - to create a new configuration,
- or -
-
Click the Edit icon [
 ] - to edit the existing configuration.
] - to edit the existing configuration.
Copy the information below from FortiMail Workspace Security into SentinelOne:
FortiMail Workspace Security
SentinelOne
Configuration name
Configuration name:
-
Windows: Sha256
-
Linux: Sha256 Linux
-
Mac: Sha256 Mac
Platform
Platform: Windows, Mac, or Linux
Account
Account: The name of your organization.
Configuration data
Configuration data:
{
"mgmtReportedHashes": 3
}
-
-
Click Next, and repeat the above copy-and-paste operations for any other operating system configuration dialog boxes that appear. You may have to repeat it for Windows, Linux, and Mac.
Your FortiMail Workspace Security-SentinelOne integration should now be functional...
Step 3: Verifying the integration
A while after performing the integration procedure above, you can verify that the integration is functioning, as follows
-
In FortiMail Workspace Security, open the Security Operations > Events page.
-
Search for "Malicious File in Endpoint" and then look for entries in the SentinelOne channel.
Flow chart diagram
See also: