This page includes:
About email phishing simulation campaigns
From time-to-time, some organizations run simulation email campaigns to determine how their employees respond to phishing attacks and to other malicious attacks. Applications such as KnowBe4 and Terranova Security are frequently used to perform these simulation campaigns. Before you begin a campaign, you must make sure that:
-
the simulation emails won't be scanned by FortiMail Workspace Security - and found to be malicious or spam
-
links inside the simulation emails won't be clicked by FortiMail Workspace Security
-
your email service won't quarantine any of the simulation emails
-
the FortiMail Workspace Security IR Team won't investigate any simulation scan that is reported by an end-user
What is the "global simulation application allowlist"
FortiMail Workspace Security maintains a list of the popular phishing simulation applications. This list is called the "global simulation application allowlist". For each application in the list, FortiMail Workspace Security maintains a list of the IP addresses that are used by each simulation application to send the simulation emails. For details, see Global simulation application allowlist below.
Before you begin
|
Important: We recommend that before you begin an email phishing simulation campaign, you first send a few trial emails to make sure that everything is operating as expected - before you begin the actual simulation campaign. |
What you need to do
Before you begin a campaign, make sure that the following prerequisites are in place:
Step 1 - Allow-list your simulation application IP addresses in FortiMail Workspace Security
There are two ways in which simulation application IP addresses - from which the simulation emails will be sent by your simulation application - can be allow-listed in FortiMail Workspace Security:
|
1 |
Your simulation application IS in the "global simulation application allowlist" Check the list below [Global simulation application allowlist] to find out if your simulation application is included in the FortiMail Workspace Security "global simulation application allowlist". If it is included, then it is not necessary for you to allow-list these IP addresses - they are already allow-listed. |
|
2 |
Your simulation application is NOT in the "global simulation application allowlist" If your simulation application is not included in the FortiMail Workspace Security "global simulation application allowlist", then:
For details, see Configuring the "sender IP allowlist" |
Step 2 - Allow-list your simulation application domains and/or IP addresses in your email service
Make sure that the domains and/or IP addresses from which the simulation emails will be sent by your simulation application are allow-listed in your email service.
For procedural details, see the official documentation for your simulation application.
Step 3 - Prevent third-party phishing simulation emails from going to quarantine
The procedure below helps to prevent third-party phishing simulation emails from going to quarantine after they are scanned by FortiMail Workspace Security.
Important: For Microsoft 365 Inline integrations only
|
Note:
|
-
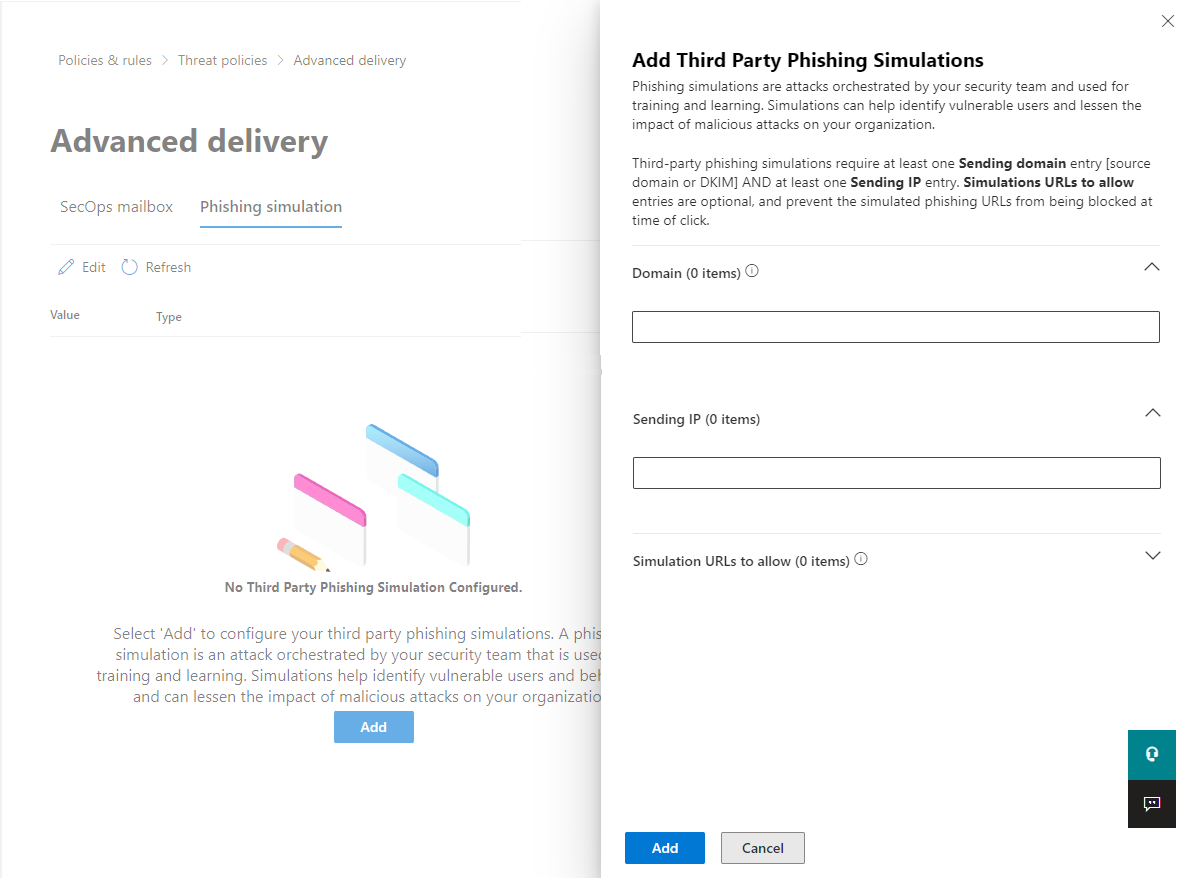
Open the Advanced delivery page in Microsoft 365.
[See here: https://security.microsoft.com/advanceddelivery
 ]
] -
Open the Phishing simulation tab.
-
Click Add or Edit.
-
Add the following domains in the Domain field:
-
the domain or domains of your simulation application
-
the FortiMail Workspace Security domain:
-
For US environments:
nat.perception-point.io
-
For EU environments:
nat.eu.perception-point.io
-
For AUS environments:
nat.aus.perception-point.io
 What is the environment of your organization
What is the environment of your organization 
-
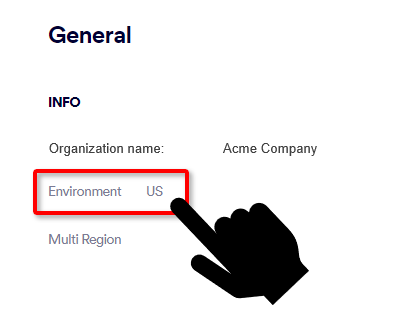
In FortiMail Workspace Security, go to Settings > Account.
-
The Environment of your organization will appear under General > Info: US, EU, or AUS.
-
-
-
Add the following IPs in the Sending IP field:
-
the IPs of your simulation application
-
the following FortiMail Workspace Security IPs:
 What is the environment of your organization
What is the environment of your organization 
-
In FortiMail Workspace Security, go to Settings > Account.
-
The Environment of your organization will appear under General > Info: US, EU, or AUS.

For US environments
For EU environments
For AUS environments
-
3.81.182.154
-
3.93.155.149
-
3.95.118.12
-
3.95.142.181
-
54.227.64.76
-
52.12.169.124 [required only if Muti-region is enabled]
-
99.81.216.78
-
34.249.190.60
-
108.128.137.108
-
99.80.189.20
-
52.12.169.124 [required only if Muti-region is enabled]
-
13.236.255.231
-
54.66.125.250
-
52.12.169.124 [required only if Muti-region is enabled]
Note: Microsoft allows you to add a maximum of 10 entries. If you are not able to add all the required IPs, you may need to insert only the primary FortiMail Workspace Security IP. For details, contact FortiMail Workspace Security Support [support@perception-point.io]
-
-
-
Click Add
Step 4 - Test the configuration
We recommend that before you begin an email phishing simulation campaign, you first send a few trial emails to make sure that everything is operating as expected - before you begin the actual simulation campaign.
Global simulation application allowlist
FortiMail Workspace Security maintains a list of popular simulation applications, and the IP addresses associated with these simulation applications. This list of simulation applications is called in the FortiMail Workspace Security "global simulation application allowlist". If your simulation application is already included in the "global simulation application allowlist", it is not necessary for you to allow-list the simulation application's IP addresses in FortiMail Workspace Security for your organization.
|
Note: Even if your simulation application is included in the FortiMail Workspace Security "global simulation application allowlist", make sure to allow-list the IP addresses of your simulation application in your email service. See Step 2 - Allow-list your simulation application domains and/or IP addresses in your email service above. |
Following is a list of the simulation applications that are included in the "global simulation application allowlist":
|
|
Application |
Simulation tag |
|---|---|---|
|
1 |
Breach Secure Now |
breachsecurenow |
|
2 |
CanIPhish |
caniphish |
|
3 |
Cofense |
cofense |
|
4 |
Cybeready |
cybeready |
|
5 |
CyberNut |
cybernut |
|
6 |
Cywareness |
cywareness |
|
7 |
Dcoya |
dcoya |
|
8 |
FortiPhish |
fortiphish |
|
9 |
Infosec |
infosec |
|
10 |
KnowBe4 |
knowbe4 |
|
11 |
Kymatio |
kymatio |
|
12 |
Reflex |
reflex |
|
13 |
Sophos |
sophos |
|
14 |
Terranova Security |
terranovasecurity |
|
15 |
Wizer |
wizer |
Listing all simulation scans
In the Security Operations > Scans page, it is possible to display only those scans that have a simulation tag.
To display only those scans that have a simulation tag:
-
In the Scans page, open the Advanced filters feature. For details, see Advanced filters.
-
Scroll down the list of filter options, and then under Detection select Only Simulation.
-
Click "Apply Filters" to display a list of simulation scans.
Adding a simulation tag to scans
If your allowlists for the simulation application's IPs and domains are correctly configured, FortiMail Workspace Security will add a "simulation" tag to each simulation scan.
|
Note: You can't request an investigation of an email that has been assigned a simulation tag. |
How does a simulation tag help?
A simulation tag helps in two ways:
-
It enables the FortiMail Workspace Security IR Team [and admin users] to identify the email as a simulation email. This prevents anyone from changing the scan verdict from Clean to any other verdict - when using the Request Investigation or Change Verdict features.
-
It enables admin users to list all the simulation scans - in the Scans page.
|
Perform the procedure below to list all the scans that were assigned a specific simulation tag:
|
How is a simulation tag added to a scan
There are two ways that a simulation tag can be added to a scan:
-
Each IP address in the "global simulation application allowlist" is associated with a simulation tag - for example Simulation-knowbe4 or Simulation-cymulate. When a scan is performed on an email that originates from an IP address that is included in the "global simulation application allowlist", the associated simulation tag is added to the scan.
For a list of the exact simulation tags that are added, see Global simulation application allowlist above.
-
The "Simulation" tag is added to scans for emails that originate from an IP addresses that is not included in the "global simulation application allowlist" - but that you added to the "Sender IP allowlist". See Step 1 - Allow-list your simulation application IP addresses in FortiMail Workspace Security above.
Remember to ask FortiMail Workspace Security Support for the exact name of the simulation tag that they applied. This will enable you to "filter or list" simulation scans.
Integrating the KnowBe4 Phish Alert button - PAB
Users of KnowBe4 are able to integrate the KnowBe4 Phish Alert button - PAB - with FortiMail Workspace Security. When integrated, when a user uses the PAB to report a suspicious email, a copy of the report is sent to FortiMail Workspace Security. This enables the FortiMail Workspace Security IR Team to investigate the email.
For additional information about the KnowBe4 Phish Alert button, see the official KnowBe4 documentation.
The KnowBe4 Phish Alert button can be integrated with any of the following FortiMail Workspace Security integrations:
-
Microsoft 365 Inline
-
Microsoft 365 API
-
Google Workspace
The procedure below shows how to integrate the KnowBe4 Phish Alert button with Microsoft 365 Inline and API integrations.
-
For details on how to integrate the KnowBe4 Phish Alert button with Google Chrome, see the official KnowBe4 documentation
 .
.
To integrate the KnowBe4 Phish Alert button:
-
Login to the KnowBe4 Dashboard [https://training.knowbe4.com/ui/dashboard]
-
Click Account Settings. [https://training.knowbe4.com/ui/account/info#phishalert]
-
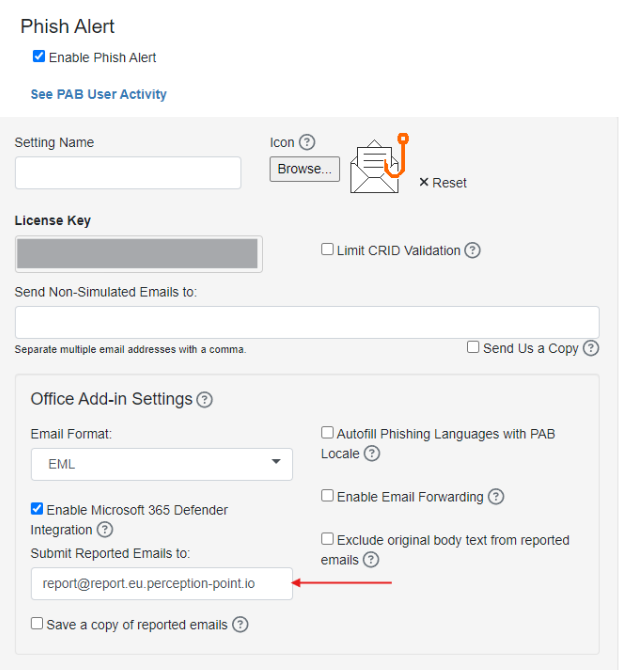
Navigate to Account Integrations > Phish Alert.
-
Select the Enable Phish Alert check box.
-
Select "Enable Microsoft 365 Defender Integration".
-
In the Submit Reported Emails to field, enter the FortiMail Workspace Security dedicated mailbox that is appropriate for your environment:
 What is the environment of your organization
What is the environment of your organization 
-
In FortiMail Workspace Security, go to Settings > Account.
-
The Environment of your organization will appear under General > Info: US, EU, or AUS.

Environment
Dedicated mailbox
For US environments
report@report.us.perception-point.io
For EU environments
report@report.eu.perception-point.io
For AUS environments
-
-
Save the settings.
The integration is now complete. Test the integration on an email that has been scanned by FortiMail Workspace Security.
|
|
See also: